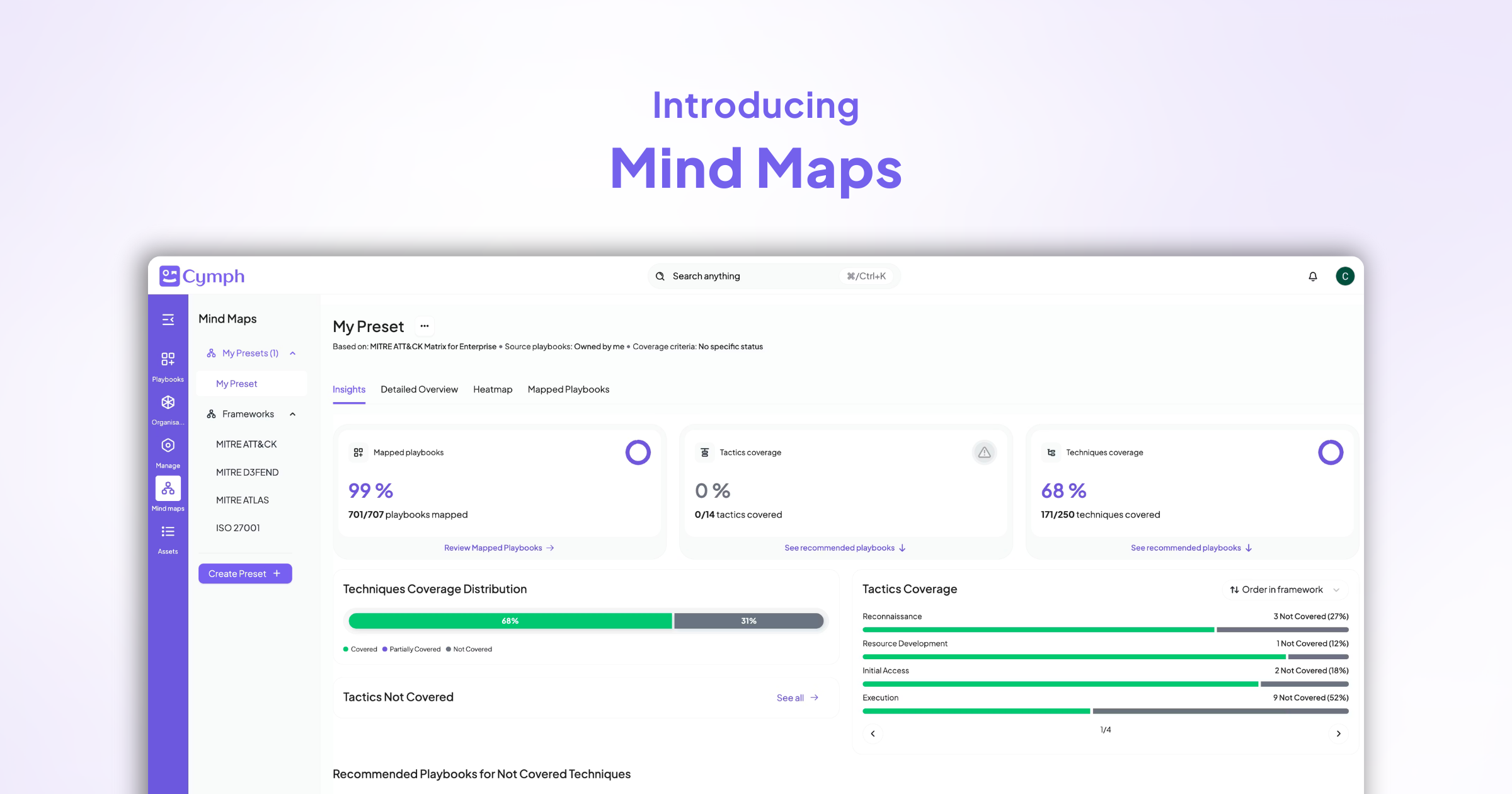
Playbooks vs. Runbooks in Cybersecurity: What’s the Difference?
Discover what’s the difference between a playbook and a runbook, why you need both, and how to use them together.

In cybersecurity, it is common to come across the terms playbook(s) and runbook(s). These terms are often used interchangeably, but in doing so, we miss the vital distinction that would allow security teams to coordinate, execute, and scale their response efforts better.
What are cybersecurity playbooks and runbooks?
What playbooks are
A playbook is basically the strategic framework which defines out the “how,” “what,” “when,” and “who” in an incident response or any other kind of cybersecurity operation. You can think of it as part of the orchestration layer that can span across technical, legal, PR, and compliance domains. It outlines to the teams how to approach a number of different incidents, e.g., phishing campaign, ransomware outbreak, or privilege escalation, and provides the decisions that need to be made, who to be involved, when to do the escalation to management, and what communication channels should be activated both internally and externally.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), for example, has created standardised federal playbooks to ensure cross-agency coordination in both incident and vulnerability response scenarios, emphasising how foundational this type of structure has become in modern security postures.
What runbooks are
Runbooks, on the other hand, are the executable part of cybersecurity operations. They provide detailed, machine readable and executable, precise actions for the technical tasks outlined in a respective playbook. These include minimal intervention actions such as connecting to hosts, performing basic forensics actions, disabling a compromised user account, applying rules to isolate a suspicious host, searching and enhancing logs for indicators of compromise, or blocking IP addresses at the firewall.
The difference and interplay between playbooks and runbooks
While playbooks are typically reviewed and maintained in high-level manner and across cross-functional teams, runbooks are mostly designed for rapid execution, often fully automated, by Level 1 and Level 2 SOC analysts, engineers, or SOAR platforms.
For example, if a playbook might direct you to investigate lateral movement, the corresponding runbook would include the commands to pull logs from EDR, verify hashes, and issue containment actions via endpoint tools.
In essence, playbooks answer the questions: “What should we do?”, “how to do it?”, “who should do it?”, and “what are all the procedural steps of the process?”
While runbooks answer: “How exactly do we do it?”, “which systems or assets need to involved?”, “which security systems are triggered?”, and ”who (human or machine) executes each action?”.
To summarise, playbooks and runbooks aren’t competing formats. They are complementary and co-dependent components for creating mature, scalable, and interoperable cybersecurity processes. Playbooks initiate the response by providing a common operating picture, aligning the responding teams across (and beyond) the organisation, and triggering decision points. Runbooks implement those decisions with precision and speed, often through semi- or hyper-automation via integration with SOAR platforms.
Together, they form a closed-loop system: one provides the strategic direction, the other delivers operational execution. Organisations that treat them as such benefit from faster incident response times, fewer errors, and more confidence during high-stakes events.

Use case scenario: How playbooks and runbooks work together
A use case for how playbooks and runbooks can be used together can be depicted in the following scenario:
“From whichever knowledge management system used to host all of the organisation's cybersecurity processes, a SOC analyst pulls the phishing playbook (based on the type of phishing he's facing, e.g. general campaign, or spear phishing, etc) to decide if a suspicious email should be blocked, escalated, or just reported as safe.
Following the process defined in the playbook, the email is confirmed to be malicious, so the analyst executes the respective runbooks that disable the user account, pull related emails, and update SIEM logs.
If the incident meets legal or regulatory thresholds, the playbook also directs the analyst to notify the Compliance Officer, who uses their own reporting playbook to prepare and submit a report to the national cyber authority within the required timelines.”
In this scenario, the playbook defines the what and when, while the runbooks define the how. Together they ensure analysts, engineers, and compliance teams stay coordinated and respond efficiently to the incident.
Best practices for aligning playbooks and runbooks
It is important for organisations to maintain both playbooks and runbooks. This is something that is constantly reinforced by research and operational trends as systems grow in complexity and interdependences.
For example, the IBM Cost of a Data Breach Report 2023 found that organisations with an incident response team and regularly tested their response plans saved an average of $1.49 million USD compared to those that did not.
Yet even with documented processes, organisation are still experiencing significant outages, which is often due to outdated or overly generic runbooks and siloed playbooks that weren’t accessible by all stakeholders. Many are still writing playbooks in static formats (like PDF or other types of documents) with limited collaboration,sharing, and execution capabilities.
Moreover, in most cases, they fail to properly convert those playbooks to actionable runbooks, which leads to delays, manual errors, and a lack of consistency.
Effective cyber processes require both playbooks and runbooks to be depend on clear, consistent documentation tailored to users’ roles – e.g. technical staff for runbooks, and decision-makers for playbooks.
Best practices concerning playbooks and runbooks include:
- Modular Design: Build playbooks as modular components that can be reused across workflows, reducing duplication and enabling flexible, cross-functional use.
- Open Standards Compatibility: Leverage open formats like CACAO (Collaborative Automated Course of Action Operations) to link or convert playbooks into executable runbooks and foster automation and interoperability across tools.
- Visual Representation: Use clear, visual playbook representations to improve understanding and usability across both technical and non-technical teams, and enhance alignment and response efficiency.
- Cyber-Specific Knowledge Management: Use platforms purpose-built for cyber process collaboration to boost sharing and institutional knowledge retention, and drive faster, more coordinated responses.
- Version Control & Testing: Maintain clear version histories and conduct regular simulations to ensure processes remain current, actionable, and effective under real-world pressure.
- Role-Based Collaboration: Support structured contributions, embedded cross-references, and permission-based sharing to increase both transparency and agility across diverse teams.
When playbooks can be easily adapted, shared, and executed across environments, organisations can respond more consistently and scale their cyber processes with more confidence and minimal interruption to their standard operations.
Conclusion
With the rise in cybersecurity threats, having up-to-date, testable, repeatable and actionable playbooks and runbooks becomes essential – even for organisations with only basic cyber processes.
Having these tools in place ensures that whether your team is facing a general phishing campaign or a sophisticated zero-day exploit, everyone – from the low-level analysts to the PR team – knows their role, and every critical task, either technical or operational, is carried out following a specific response plan and accurately.
Investing in this structured approach, and maintaining it through regular iterations and updates after post-incident reviews, can be the difference between successfully containing a threat or letting chaos unfold.