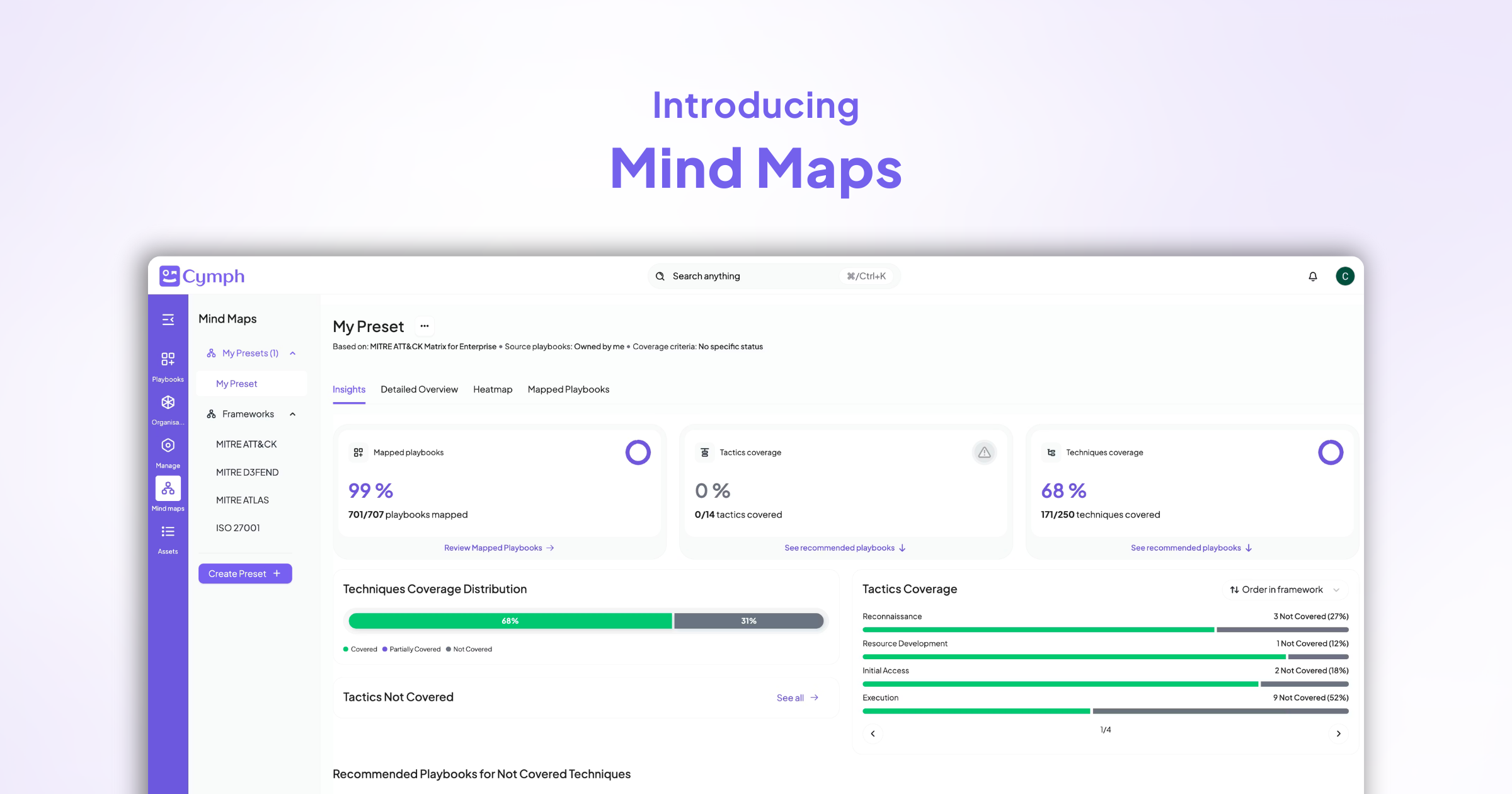
Why We Founded Cymph
Discover the founding story of Cymph and why we exist.

The year is 2024. It all started with a simple yet striking observation: the current way we author, manage, and share cybersecurity processes is slow, fragmented, and still reliant on manual work. Teams often use a combination of wikis, PDFs, emails, and file sharing to document their cybersecurity processes and collaborate. It felt risky and outdated for a domain evolving as fast as cybersecurity.
We were intrigued by that challenge. We remembered that we have seen a similar pattern with threat intelligence before: back in the old days, we were sharing indicators of compromise via email, wikis, and file sharing, and then manually updating firewall rules and intrusion detection systems.
The fragmentation and vendor lock-in problem
It didn’t take us long to verify that the playbook universe is fragmented. Either this is the format being used, the hosting solution in place, or the language that it's written in, there is no uniformity when it comes to playbooks. A quick web search for “cybersecurity playbooks” was enough to confirm this.
On one hand, playbooks are scattered around general purpose tools: knowledge management systems, PDFs, Word documents, Wikis for documenting cybersecurity processes, as well as email, file sharing, or git-based solutions for sharing these processes. These widely-adopted solutions are preferred for their quick editing and collaboration features.
On the other hand, you can find playbooks inside SOAR and workflow automation platforms. These products are built for teams that specialise in automations around threat response and incident management. These playbooks are written in proprietary languages that are not interoperable – making them hard to share across defenders.
The current way of managing cyber processes cannot scale
Cyber attacks never slow down. Their volume and complexity is growing year over year, leaving defenders scrambling around for time and resources. At the same time, new and evolving regulatory requirements continue to raise the stakes – adding even more operational pressure. It’s becoming increasingly clear: the current way of managing cybersecurity processes simply doesn’t scale.
Effective protection depends on collaboration and knowledge sharing across teams. But the tools in use today weren't built for this. General purpose tools may be accessible and easy to use, but they're not machine-readable and force teams to manually translate processes into their SOARs and automation platforms. Meanwhile, these specialised platforms may be powerful for execution, but they are often siloed and hamper collaboration – especially for stakeholders outside the core security team
As a result, we see organisations having to deal with problems like locating their playbooks, keeping them up-to-date, copy-pasting commands from Wikis to their automation platforms. Teams are still emailing process documents or tossing them into shared drives, with bookmarks as the only way to locate them again.
There’s a clear gap between these two existing approaches. And this gap forces organisations to work around their tools instead of being supported by them. Over time, we came to see this as the root cause of why cybersecurity processes don’t scale – and why something fundamental needs to change.

This is why we started Cymph
We founded Cymph to address this systemic problem in cybersecurity. Cyber process collaboration is broken. And when process collaboration breaks, everything downstream – from speed to resilience to compliance – starts to break with it. We believe cybersecurity needs its own cross-functional process layer, one that connects people, tools, and workflows without forcing tradeoffs between collaboration and execution.
Modern cybersecurity teams must have a single way to manage, share, and execute their processes. And this way must be tightly integrated with the rest of the cybersecurity ecosystem. This is why designed a platform that:
- Allows the creation and management of cyber processes in a vendor-agnostic fashion.
- Promotes collaboration and community building.
- Creates an orchestration and interoperability layer across different products.
- Allows teams to focus on process design that is shareable and visible within and across their organisation.
- Minimises the time and risk to translate processes into actionable workflows.
- Acts as a single source of truth when it comes to cyber-processes.
Cybersecurity today is a team sport. All stakeholders – security, compliance, legal and engineering – should be able to contribute to and benefit from clear, actionable, and shared processes. There is only one way to scale up: focusing on the “what” needs to be done and not the “how”. That’s why we built Cymph. Because cybersecurity deserves its own layer for cyber process collaboration.